Understanding How VPN Works: A Comprehensive Guide for Beginners
Ever felt a shiver down your spine when connecting to a public Wi-Fi network? Or perhaps you’ve pondered the invisible hands that could snatch your sensitive data mid-transit? Fear not, for the solution lies in understanding how VPN works—a digital superhero in the realm of online privacy and security.
In this guide, we’ll embark on a thrilling adventure through the virtual corridors of Virtual Private Networks (VPNs), unveiling their hidden powers and uncovering the mysteries of their operations. Whether you’re a curious beginner or a seasoned tech enthusiast, prepare to be enlightened as we explore the depths of how VPNs work and how they can shield you from digital threats.
What is a VPN?
At its core, a VPN, or Virtual Private Network, acts as a digital fortress, safeguarding your online activities from prying eyes and potential threats. Picture it as a secret passage through the chaotic maze of the internet, where your data travels incognito, shielded from the gaze of cyber predators.
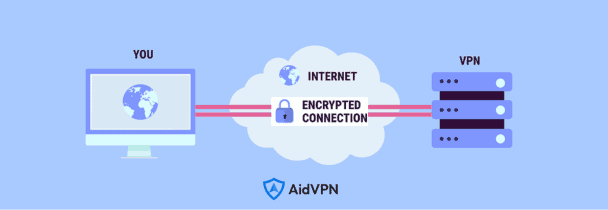
But how does VPN work its magic? By weaving a cloak of encryption around your digital footprint, VPNs transform your ordinary internet connection into a secure tunnel, shielding your data from interception and eavesdropping. This encrypted tunnel serves as a virtual conduit, guiding your online interactions safely from point A to point B without leaving a trace of your digital footsteps.
In essence, VPNs create a private enclave within the vast expanse of the internet, where your data enjoys the utmost protection and confidentiality. So, the next time you connect to a public Wi-Fi network or browse the web from the comfort of your home, remember the silent guardian watching over your digital adventures—your trusted VPN.
How VPN Works
A. Encryption Process
When we delve into understanding how VPN works, encryption emerges as its cornerstone, fortifying your digital fortress against potential intruders. Think of encryption as the secret code that renders your data indecipherable to anyone without the key. By scrambling your information into an unreadable format, VPNs ensure that even if intercepted, your data remains secure and confidential.
To achieve this feat, VPNs employ sophisticated encryption algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest–Shamir–Adleman), renowned for their robustness and reliability. These algorithms serve as the digital locksmiths, transforming your plaintext data into an impenetrable cipher, ready to traverse the treacherous realms of the internet unscathed.
B. Routing Mechanism
Now, let’s peel back the layers of VPN’s routing mechanism—a labyrinth of digital pathways guiding your encrypted data through the vast expanse of the internet. Unlike traditional internet connections that follow a direct route from sender to receiver, VPNs navigate a circuitous path, bypassing potential hazards and adversaries along the way.
Through the magic of VPN routing, your data embarks on a journey through a secure tunnel—a virtual conduit shielded from prying eyes and malicious actors. This secure tunnel acts as a clandestine passage, ensuring that your data remains safe and untouched by the perils of cyberspace.
C. IP Address Masking
One of the most captivating aspects of how VPN works is its ability to cloak your digital identity through IP address masking. Picture your IP address as your digital fingerprint—a unique identifier that traces your online activities back to your virtual doorstep. With VPNs, however, anonymity reigns supreme as they shroud your true IP address in a veil of secrecy.
By replacing your original IP address with an anonymous one from their vast pool of servers, VPNs obscure your digital footprint, rendering you invisible to prying eyes. This IP address masquerade not only shields your identity but also grants you the freedom to explore the digital realm without constraints or surveillance.
D. Tunneling Protocols
In the realm of VPNs, tunneling protocols serve as the guardians of secure data transmission, ensuring that your information traverses the digital highways unscathed. These protocols govern the rules of engagement within the VPN tunnel, dictating how data is packaged, encrypted, and delivered to its destination.
From the robust encryption of OpenVPN to the speed and efficiency of L2TP/IPsec and the reliability of IKEv2, VPNs employ a diverse array of tunneling protocols to cater to varying needs and preferences. Each protocol brings its unique strengths to the table, ensuring that your data remains shielded from interception and tampering throughout its journey.
Advantages of Using a VPN
A. Privacy Protection
In the ever-expanding digital landscape, privacy has become a precious commodity, constantly under siege from prying eyes and data-hungry entities. Here’s where VPNs step in as the guardians of your digital sanctuary. By employing advanced encryption techniques, VPNs cloak your online activities in a veil of secrecy, rendering them indecipherable to would-be snoopers and hackers.
Moreover, VPNs play a pivotal role in thwarting surveillance and tracking attempts by ISPs, government agencies, and other entities keen on monitoring your online behavior. With VPNs at your side, you can navigate the digital realm with confidence, knowing that your privacy remains intact, shielded from prying eyes.
B. Security Enhancement
While privacy protection forms the first line of defense in the battle for online security, VPNs offer an additional layer of fortification through IP address masking. By substituting your real IP address with one from a remote server, VPNs cloak your digital identity, making it virtually impossible for adversaries to trace your online activities back to you.
Furthermore, VPNs serve as stalwart sentinels against cyber threats and hacking attempts, erecting virtual barriers that deter malicious actors from infiltrating your digital domain. With VPNs, your online presence becomes fortified against potential breaches and intrusions, ensuring that your sensitive data remains safeguarded from prying eyes.
C. Access to Restricted Content
In a world where digital borders and censorship barriers abound, VPNs emerge as liberators, offering a gateway to unrestricted online content. By circumventing geo-blocks and censorship measures, VPNs empower users to access region-locked websites, streaming services, and online platforms with ease.
Whether you’re traveling abroad or simply seeking access to exclusive content, VPNs serve as your passport to the global internet, transcending geographical barriers and granting you unfettered access to the digital world. From unlocking streaming libraries to bypassing online censorship, VPNs enable you to explore the vast expanse of cyberspace without constraints.
Disadvantages of Using a VPN
While VPNs offer a fortress of security in the digital wilderness, they aren’t without their pitfalls. Let’s delve into some of the drawbacks you may encounter when harnessing the power of VPNs and explore ways to navigate these challenges.
A. Decreased Connection Speed
One of the most common grievances among VPN users is the potential for reduced internet speed. As your data traverses through the encrypted tunnel of a VPN, it may encounter additional latency and overhead, resulting in slower connection speeds compared to direct internet access.
Several factors can contribute to this sluggishness, including the geographical distance between your device and the VPN server, the encryption strength used by the VPN protocol, and the overall load on the VPN server.
To mitigate speed issues while using a VPN, consider connecting to servers closer to your physical location, opting for VPN protocols optimized for speed (such as UDP-based protocols), and selecting VPN providers with robust infrastructure and optimized networks.
B. Logging Policies
Another concern associated with VPN usage revolves around logging policies implemented by VPN providers. While VPNs tout privacy and anonymity as their cornerstones, some providers may engage in logging user activity, potentially compromising your privacy and security.
It’s essential to scrutinize the logging policies of VPN providers and opt for services that uphold transparent logging practices or adhere to strict no-logs policies. By choosing VPN providers committed to safeguarding your privacy, you can mitigate the risk of your online activities being monitored or logged.
C. Legal and Regulatory Considerations
Navigating the legal landscape surrounding VPN usage can be a daunting task, as regulations and restrictions vary significantly from one country to another. While VPNs are legal in many jurisdictions, certain countries impose stringent regulations or outright bans on VPN usage.
Before deploying a VPN for your online activities, familiarize yourself with the legal implications and regulatory frameworks governing VPN usage in your region. Ensure compliance with local laws and regulations to avoid running afoul of legal authorities and mitigate the risk of facing penalties or repercussions.
By understanding the potential drawbacks and navigating the legal complexities associated with VPN usage, you can harness the power of VPNs while safeguarding your online privacy and security effectively.
Frequently Asked Questions (FAQs)
As we journey deeper into the realm of VPNs and unravel the mysteries of how VPN works, it’s natural to encounter lingering questions about their efficacy, legality, and safety. Here, we address some of the most common queries to shed light on the intricacies of VPN technology:
A. Is VPN traffic encrypted?
Absolutely! The cornerstone of how VPN works lies in its ability to encrypt your online traffic, rendering it indecipherable to prying eyes. Through sophisticated encryption algorithms like AES and RSA, VPNs cloak your data in a digital veil, ensuring its confidentiality and integrity as it traverses the vast expanses of the internet.
B. What is an always-on VPN? What is a kill switch?
An always-on VPN is a feature that automatically connects your device to a VPN whenever you access the internet, providing continuous protection against online threats. On the other hand, a kill switch acts as a failsafe mechanism, terminating your internet connection if the VPN connection drops unexpectedly, preventing any data leakage in the process.
C. Is a VPN necessary?
While not strictly mandatory, a VPN serves as a potent tool for enhancing your online security and privacy. Whether you’re browsing on public Wi-Fi networks or accessing geo-restricted content, a VPN offers an added layer of protection and anonymity, making it a valuable asset in today’s digital landscape.
D. Is a VPN 100% safe?
While VPNs significantly bolster your online security, nothing on the internet is entirely foolproof. However, by choosing reputable VPN providers with robust encryption protocols and transparent logging policies, you can mitigate risks and enjoy a safer online experience.
E. Is VPN legal in India?
Yes, VPN usage is legal in India, allowing individuals to safeguard their online privacy and access restricted content without violating any laws. However, it’s essential to use VPNs responsibly and refrain from engaging in illegal activities that may contravene local regulations.
F. Do VPNs log or store my data?
While some VPN providers claim to have a strict no-logs policy, it’s essential to exercise caution and conduct thorough research before entrusting them with your data. Although VPNs are designed to enhance privacy, choosing a trustworthy provider with transparent logging practices is crucial for maintaining confidentiality.
G. What is the main difference between a firewall and a VPN?
While both serve to bolster cybersecurity, firewalls and VPNs operate on distinct principles. A firewall acts as a barrier between your device and the internet, filtering incoming and outgoing traffic to block malicious threats. In contrast, a VPN creates a secure tunnel for transmitting data, encrypting it to safeguard privacy and anonymity. While firewalls protect against external threats, VPNs focus on securing data in transit, offering complementary layers of defense in the cybersecurity arsenal.
By addressing these FAQs, we aim to demystify the nuances of VPN technology and empower you to make informed decisions about your online security and privacy. As we continue to explore how VPN works, remember to prioritize safety and vigilance in your digital endeavors.
Final Words
In fine, we’ve embarked on a journey to unravel the mysteries of how VPN works, shedding light on its inner workings and practical applications in safeguarding online security and privacy. From its role as a digital guardian to its ability to create secure tunnels of encryption, VPNs have emerged as indispensable tools in the modern internet landscape.
By understanding how VPN works, we empower ourselves to navigate the digital realm with confidence, knowing that our data is shielded from prying eyes and potential threats. Whether you’re browsing the web from a bustling coffee shop or accessing sensitive information from the comfort of your home, a VPN stands as your silent sentinel, ensuring that your online activities remain private and secure.
In today’s interconnected world, where digital threats loom large, embracing the power of VPNs is not just a choice but a necessity. So, let us embrace the knowledge gained from this exploration and continue to harness the power of VPNs to safeguard our digital presence and protect our online privacy.





Leave a Reply
Want to join the discussion?Feel free to contribute!